Sometimes when we see that our pen drives or memory card affected by shortcut virus then we format it without knowing anything because we feel annoying most of the time seeing the ugly shortcut image just popping during a click. Shortcut virus has mainly two types;
the most common is pen drive/ Flash drive Shortcut virus, second is the File and Folder Shortcut virus.
Shortcut virus is totally Trojan virus. It combine files in your pen drive and Keep it into one hidden folder. Then, it create a shortcut.exe for pen drive.
Actually You can remove that shortcut virus from your any computer drive or removable drive.
Step-1- At first, go to start menu and then go to ‘run’ option. You can also press Windows key + R.
Step-2- Then type “cmd” into the box and press OK bottom to run command prompt.
Step-3- Then if you did not connect your infected removable drive (Pen drive, SD Card), just connect it to your computer.
Step-4- After attached the infected removable drive just type this following command in Command prompt: attrib -h -r -s /s /d H:\*.*, (Where H is the removable drive) and press Enter.
Step-5- Now you can copy data from your removable drive because the shortcut virus is fixed now.
Step-6 – After saving the data, now format your removable drive completely.
Step-7 – Then, if your removable drive formatted then copy all data back to your removable drive.
This may also be written as under : –
Insert your removable device, and notice the drive letter of your removable device. Like here it is G: and while you open by any process it will come up like this as shown.

And you will not find your data anywhere in these icons. You just need to follow simple steps after this.
- Now, open command prompt, by typing “cmd” (without quotes) in search bar in start menu.
- When command prompt pops up, just write your removable device’s drive letter, like here it is G, with a colon, like “g:” (without quotes), and hit ENTER.
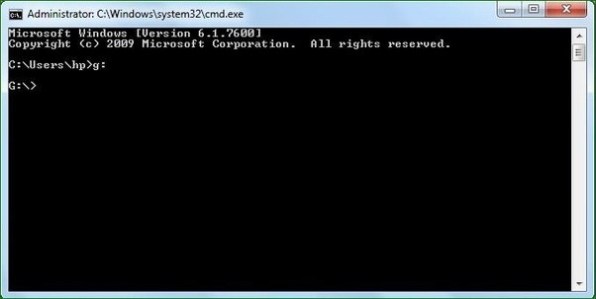
It will redirect you to that drive.
- You just need to remember this command and nothing else in this whole process, which you have to type in command prompt window,
“attrib g:*.* -a -r -s -h /s /d” (without quotes) and hit ENTER, like this:
It will retrieve your data in that drive, when you open your drive it will have a unnamed folder(here, last folder), like this:
And now, when you open this folder, Bam! You have all your data here. Like this:
with some other virus icons, which we will tackle later.
- Now, you have to write this command to delete that shortcut virus:
“del *.lnk” (again, without quotes) and again hit ENTER, like this:
Now, you will see that shortcut virus has disappeared, like this:
- Now that the virus is deleted and all your data is retrieved, Select and copy all your data somewhere, like desktop, and don’t select some unknown files, which are virus. and after copying them somewhere, Format your removable device and again put all your data in your device.